The Relationship Between Ransomware and VPNs
Photo from Pexels
Originally Posted On: https://www.alwaysvpn.com/insights/relationship-between-ransomware-and-vpns
Ransomware attacks have become so popular that gangs have begun scamming each other, if recent reports are to be believed. Take REvil (Ransomware Evil), an infamous Russian group that works with affiliates for a cut of the ransom. It transpired that their software “included a secret backdoor in its ransomware code—allegedly enabling the ransomware group to steal illicit ransom proceeds from its affiliates.”
REvil was involved when meat giant JBS was forced to temporarily shut down some of their operations in Australia, Canada, and the US after their networks were hacked. JBS ended up paying an $11 million ransom in Bitcoin. Stories like this are a dime a dozen these days, and there are no signs of them slowing down. Quite the contrary, really.
Here’s what you need to know about ransomware and VPNs, including how to prevent attacks and what common scams you should be aware of.
What Is Ransomware?
Malware, or malicious software, is used for anything from stealing data to secretly using your hardware to mine cryptocurrencies. Ransomware is a form of malware that can prevent the user from accessing their files or hardware because they have been stolen, deleted, or encrypted. Whatever the method, the aim is to extract money from the user in the form of a ransom. (That’s how it earns the moniker.)
An infamous example would be the 2017 WannaCry ransomware attack which was estimated to have affected more than 200,000 computers across 150 countries.
It targeted computers running the Microsoft Windows operating system and used an exploit called EternalBlue which was originally developed by the NSA. In the 2017 outbreak, the payload encrypted thousands of files and left behind a ransom note with instructions to pay $300 in Bitcoin to recover the files.
(As a side note, it drove the price of the cryptocurrency to an all-time high as it surged to over $2,500 per coin. As of October 2021, the price is now $48,000.)
WannaCry is one of many advanced malware applications, with Xafecopy being another that has made headlines in the past. Primarily targeting users in India, Russia, Turkey, and Mexico, Xafecopy is usually disguised as an app for Android systems, such as a battery saver or an alarm. It uses WAP billing to extract payment from the user.
“WAP billing” is an archaic mechanism for consumers to buy content from Wireless Application Protocol (WAP) sites, being charged directly via their mobile phone bill. Some carriers still offer basic support for the feature. (For anyone old enough, think back to buying ringtones and backgrounds in the early 2000s.)
WAP billing has been actively abused by cybercriminals who have added the ability to open Web pages that have WAP billing and initiate payments while the user suspects nothing.
While the Xafecopy trojan is a form of malware, it’s not ransomware. After all, it doesn’t lock your device or steal your data, and it aims to extract smaller payment amounts, rather than the large sums seen in recent years.
Ransomware Stats in 2021
Ransomware has become a big problem over the last few years, fuelled by the ease of use for criminals and the enormous potential gains. Here are stats, facts, and figures about a burgeoning black market.
- Antivirus firm Emsisoft found that the average requested ransomware fee increased from roughly $5,000 in 2018 to about $200,000 in 2020. This is likely to increase year over year.
- Ransomware is expected to attack a business every 11 seconds by the end of 2021.
- It was predicted that global ransomware damage costs will reach $20 billion by 2021, while the FBI’s Internet Crime Complaint Center (IC3) estimated ransomware losses at $29.1 million last year. In other words, it’s more prevalent than you might have guessed.
- Meanwhile, the true cost is thought to be much higher due to unreported losses stemming from ransomware demands.
- Sophos’ 2021 annual ransomware survey found that 37% of respondents’ organizations were hit by ransomware in the last year, defined as multiple computers being impacted by a ransomware attack but not necessarily encrypted. This is a significant reduction compared to the 51% seen in 2020.
- Sophos noted that the average ransom paid by mid-sized companies cost $170,404. This tracks with Emsisoft’s findings.
- On average, 65% of encrypted data is restored after a ransom is paid. This should go without saying, but you can’t trust an extortionist to follow through with their promises.
Common Ransomware Scams
What are common ransomware scams to be aware of, and what should a potential victim expect? We break the two main tactics cybercriminals use.
Scareware
Scareware is a more traditional form of malware, often used to manipulate the user into visiting a suspicious website or downloading a dodgy file. The end goal can be getting you to sign up for an unnecessary paid service or to extract payment via cryptocurrencies.
It’s named as such since the goal is to “scare” the user into paying up. For example, it’s often found on mobile device browsers, telling the user that they need specific software to access a service. It may come through as a pop-up notification that says your device has been infected in an attempt to get you to download a compromised app.
It’s typically easy enough to avoid, as long as you’re able to ignore the scare tactics. A few key ways to tell a serious notice apart from a scareware attack is to look at the design and grammar the sender uses. They often use lots of red colors and exclamation points and may have typos or weird wording throughout the message.
Doxware
Doxware, or extortionware, is when the hacker gains access to sensitive data. This can include anything from work-related files to personal emails or chat logs. The key aspect is that it threatens to expose the user in some shape or form.
Compared to scareware, doxware is more dangerous. It leads to criminals that have access to sensitive data, which can be used to extort large amounts of money. Anyone can be the target of a doxware attack. To this end, companies tend to be the target, as they have the resources necessary to pay larger ransom demands. (This doesn’t mean that individuals can’t fall prey, too.)
Ransomware will often ask for cryptocurrency as a method of payment. They do so as it can be received anonymously, with no way to get the money back via traditional means. Extortionware often uses traditional malware to gain access to accounts or resources. Unlike other forms of doxware, they aim to use data exfiltration to blackmail individuals or organizations.
For example, in April 2021, REvil claimed that it had accessed the internal computers of Taiwan-based Quanta and managed to obtain several images and schematics of unreleased Apple products. They wanted $50 million, moving to blackmail Apple directly after Quanta refused to play ball. (There’s no end to the story, as REvil removed their demands later that month, and Apple refused to comment on the saga.)
The point is, it doesn’t matter if Quanta were able to gain control of their systems again. The unreleased images and schematics were what REvil was hoping to use to gain payment via extortion.
Ransomware & VPNs
Many VPNs will work to comply with various law enforcement agencies found around the world. Even if they’re a no-logs service, they may keep payment info or take an email address on sign-up which can be forwarded on. (It’s one of the reasons why accepting payment via crypto is such an important feature for anonymity.)
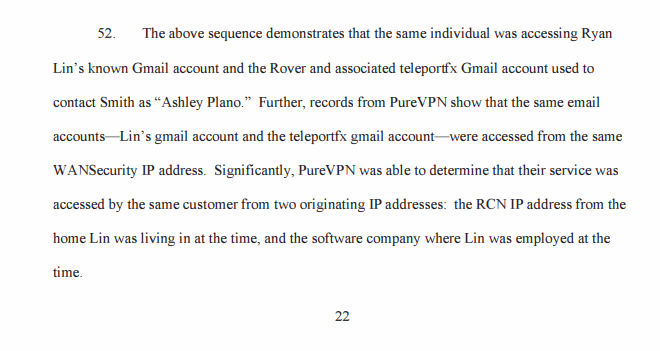
For example, take PureVPN who handed information to the FBI in a cyberstalking case back in 2017. A Department of Justice document details the ways in which the service complied with the investigation:
This is juxtaposed by the likes of NordVPN, who are based in Panama and maintain a warrant canary that states:
“We have never willingly disclosed any user data or provided any access to user traffic to any third party. We do not collect user traffic logs and have never been compelled to do so by any third party. We have not disclosed any private keys or any information of our users, and we have not been forced to modify our system to allow access or data leakage to a third party of any kind.”
These are commercial providers that can be used to provide an additional layer of anonymity while online.
Illegal VPNs
Before unleashing any ransomware, nefarious users tend to use VPN services that target criminals. One example would be Safe-Inet, which was active for more than a decade, according to Europol. Another is DoubleVPN, a service that was heavily advertised across English and Russian-speaking dark web cybercrime forums.
Both have since been shut down, with police in Europe, the United States, and Canada working in tandem as they seized their domains and servers. It makes sense given a VPNs ability to hide the user in relative anonymity.
Will a VPN stop ransomware?
In and of itself, a VPN alone won’t be enough to keep ransomware attacks at bay. In fact, compromised VPN servers represent a potential entry point for criminals. A 2021 investigation conducted by Kaspersky experts revealed that “attacks of the Cring ransomware had exploited a vulnerability in FortiGate VPN servers.”
They noted that “victims of these attacks include industrial enterprises in European countries. In at least one case, a ransomware attack resulted in a temporary shutdown of the industrial process due to servers used to control the industrial process becoming encrypted.”
However, it can help to make the user less vulnerable by encrypting your traffic and data, while hiding your IP address in the process.
Preventing Ransomware Attacks
In terms of scareware, it’s often enough to ignore their attempts to extract payment or user info. It can be tough as they’re using psychological tricks to make you think twice, but it’s best to remember that it’s likely to be a generic message sent to thousands of people at once.
If they have access to an old password that is being used to make threats, Have I Been Pwned allows you to search multiple data breaches to see if your email address or phone number has been compromised. That’s more likely to be the source of their inside information. (It’s also why a password manager tends to pay off in the long run.)
If they claim to have access to your files or your device/camera/mic, it’s exceedingly unlikely to be true. Essentially, they’re mimicking the end result of doxware, while using tactics associated with scareware.
On an organizational level
Doxware is more difficult to deal with, and any steps should be preventative in measure. After all, increasing numbers of criminal gangs continue to exploit the use of malware, and police are unable to keep up on a global scale.
A malware incident recovery plan should be set in place for all organizations, though you should expect to be attacked. The plan should involve contingencies, and what to do in multiple scenarios to limit potential damage. Employing security experts will be especially useful, as well as deploying anti-ransomware technologies.
On an individual level
Individuals are mostly targeted using scareware tactics, as it’s easy to isolate a loan sheep than a crowd. You’ll want to stay alert when messages come through your devices and always check things like the sender name and grammar of each notification.
A VPN will also help to obscure your IP address and your internet usage, as well as provide certain security features like ad blocking and HTTPS rerouting. However, it’s pointless if you can’t help but click on random files sent to your spam folders, or if your internal systems contain vulnerabilities.
The Sophos State of Ransomware 2021 survey found that the number of respondents affected had dropped but only because “many attackers have moved from larger scale, generic, automated attacks to more targeted attacks that include human-operated, hands-on keyboard hacking”.
Be especially careful in terms of passwords and phishing, and ensure that your systems are up to date.
Best VPNs for Ransomware
We’ve come up with a list containing some of the best secure VPNs if you’re worried about falling victim to ransomware. Bear in mind, they may not have built-in ransomware protection, but it still helps to keep your online movements private.
Ideally, they will also prevent scareware by blocking suspicious websites at their source.
NordVPN
NordVPN is a feature-rich VPN with strong privacy practices. For example, CyberSec is an advanced technology solution that takes your security and privacy to the next level, working to block websites known for hosting malware or phishing scams, which should help to defend against online threats such as the ones mentioned above. It also removes some ads, which could potentially speed up your browsing experience.
CyberGhost
CyberGhost VPN is a viable budget alternative thanks to adjustable privacy layers that will block ads, online tracking, and malicious websites. In our review, we’ve noted that it’s tempting if you’re looking for an all-in-one online security software package. They offer security features like an automatic kill switch and their NoSpy server locations are just a few perks that come with the service. NoSpy allows users to benefit from Romanian jurisdiction.
Surfshark
Another solid option would be Surfshark. There’s a free 7-day trial, and they boast about multiple third-party audits from Cure35, most recently a 2021 holistic audit of their logging claims and encryption methods. The VPN also has an ad blocker (branded as CleanWeb) which runs on Windows, Android, and macOS devices as well as Surfshark’s Chrome and Firefox web browser extensions.
Closing Thoughts
Ransomware can affect any individual, organization, or business – big and small. Anyone with a hint of an online presence is likely to have been exposed to scareware, yet doxware is the reason why ransomware continues to make headlines in the latter stages of 2021. It’s easy to get the two mixed up, but doxware is serious business and is projected to cost users millions of dollars in total over the next few years.
So far, VPNs have had a role to play for both attackers and defenders. For criminals, anonymity allows them to operate without having to worry about encountering the law, while new services continue to pop up with alarming regularity.
For the average user, a secure VPN helps to mask your internet usage and IP address, although it won’t keep the majority of advanced ransomware attacks at bay. Still, it can be especially useful if it comes with an ad blocker or works to prevent the user from connecting to suspicious websites in the first place.
